...
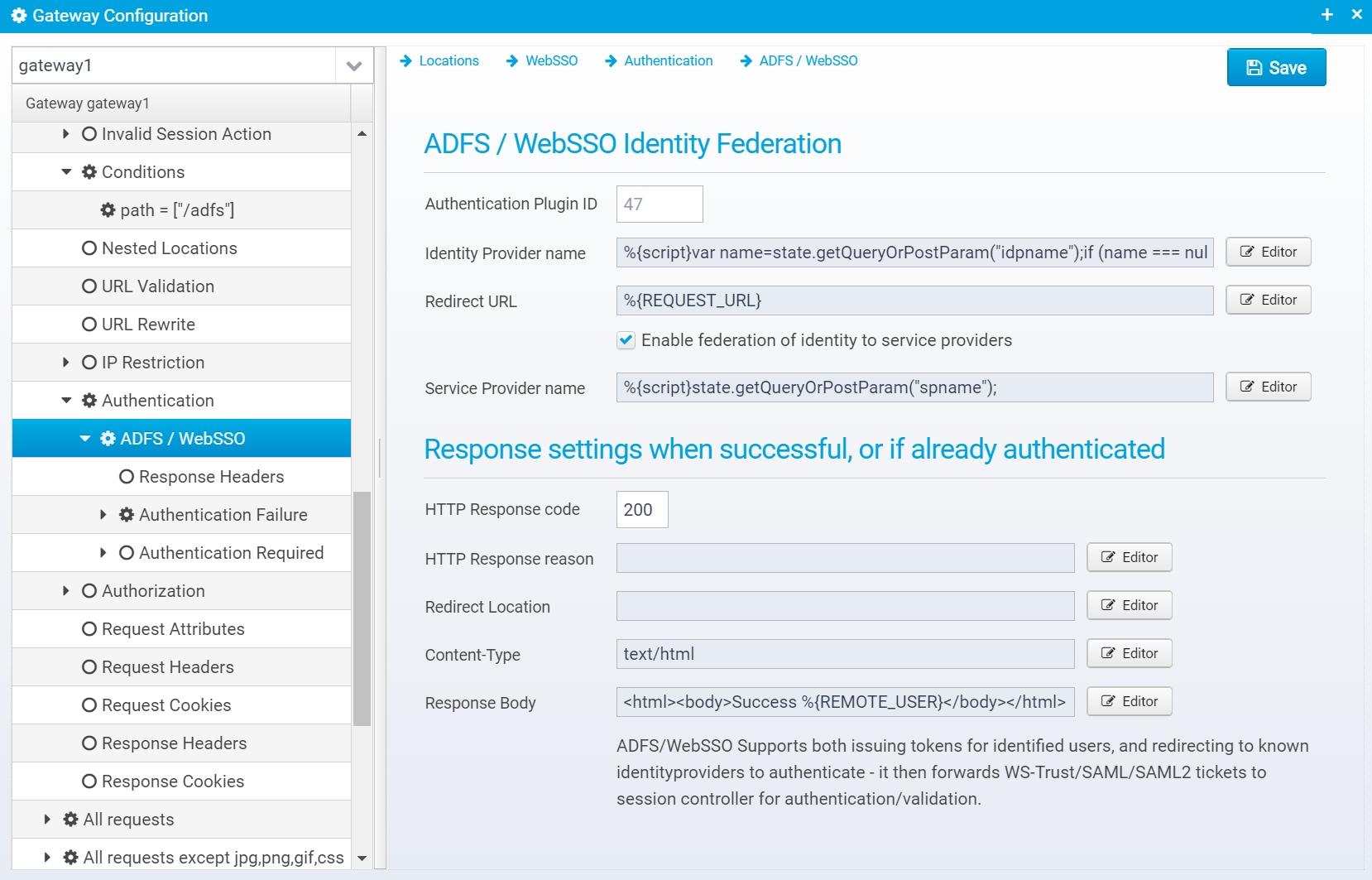
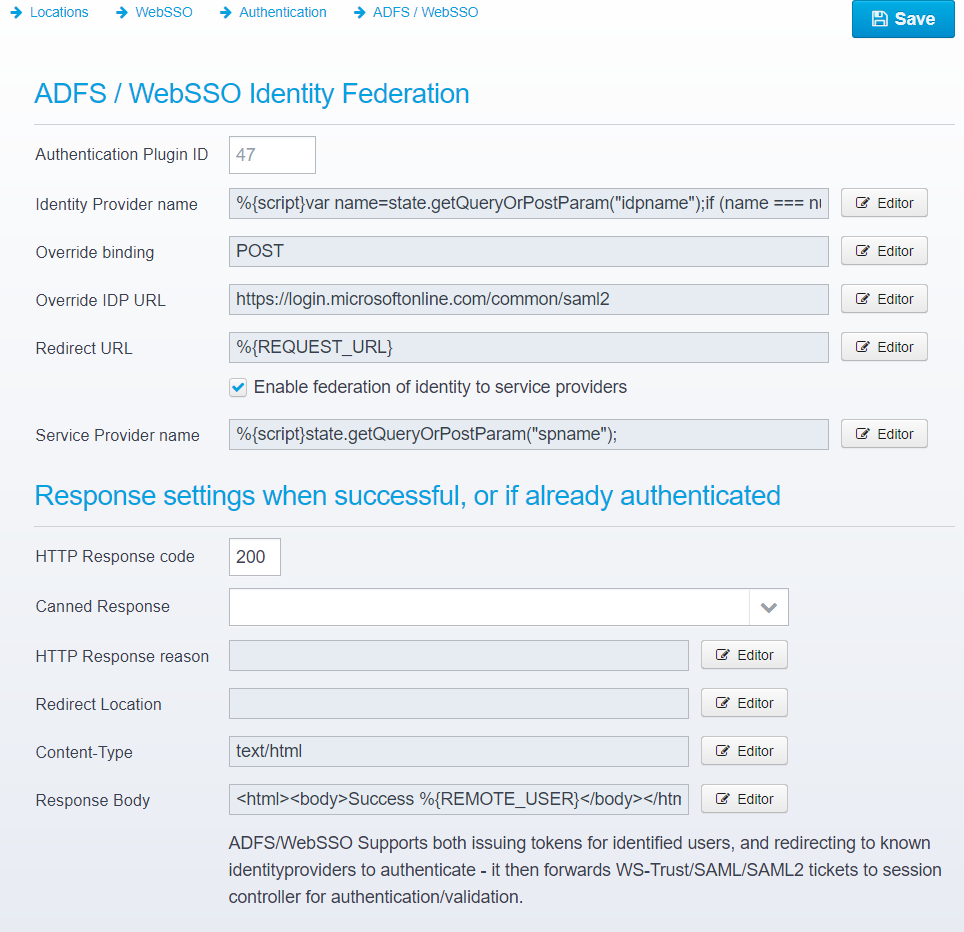
This screen is available if the authentication plugin "AuthenticatorWebSSO" is selected.
Configuration is stored in the JSON Object websso within the authentication object.
...
| Info | ||
|---|---|---|
When using another site as Identity Provider, and Ceptor as Service Provider to that site, the following additional query/post parameters can be specified when calling the URL that triggers this plugin:
For passive binding (which is the default), the redirect to the Identity Providers federation URL will be done, adding these query parameters:
For the passive binding, no SAML Request will be transmitted. for redirect / GET binding, the redirect to the Identity Providers federation URL will be done, adding the following query parameters:
Note that the SAML request will be signed/encrypted according to the query/POST input parameters signrequest and encryptrequest. for POST binding, a form is return that autosubmits sending a POST requst to the Identity Providers federation URL with the following parameters:
Note that the SAML request will be signed/encrypted according to the query/POST input parameters signrequest and encryptrequest. |
Override binding
Override the binding - normally if sending the request to a service provider, the binding is POST - in that case, either POST or redirect is supported.
If using an identity provider (if Identity Provider name is set and service provider name is not) then the binding can be set to passive/GET/POST as specified above.
Note that if this property is read, the query/POST parameter "binding" is not used.
Default: none
JSON key: override.binding
Override IDP URL
The URL of the identity provider is normally specified in the Federations configuration for each Identity Provider - by default that URL is used, but you can override the URL by specifying another here.
Default: none (uses Identity Provider URL from Federations configuration)
JSON key: override.identityprovider.url
Redirect URL
URL that the identity provider should redirect the user back to after authenticating
...