Keystore configuration
This section describes the various possibilities for configuring a Keystore containing one or more private or public keys used for signing or verification of tickets and tokens.
JSON Configuration
A keystore configuration in general con contain a lot of different entries, ranging from a keystore loaded from disk at each Ceptor server instance, to keys and certificates being configured solely within the configuration.
In general, the first private key is used for signing, unless a specific key is pointed to by setting alias.privkey in which case only this key is loaded.
Below is an illustrative example;
{
"file": "${ceptor.home}/config/x509/issuer/certissuer.pfx",
"provider": "BC",
"type": "PKCS12",
"password": "{encoded}96E1FAF9F9578720",
"alias.privkey": "abc",
"alias.cert": "public",
"password.per.alias": [],
"privatekey": "-----BEGIN PRIVATE KEY-----\nxxxxxxxx\n-----END PRIVATE KEY-----",
"certificate": "-----BEGIN CERTIFICATE----\nxxxxxxxxxxxxxx\n-----END CERTIFICATE----",
"publickey": "-----BEGIN RSA PUBLIC KEY----\nxxxxxxxxxxxxxx\n-----END RSA PUBLIC KEY----",
"password.per.alias": [
"public=anotherpassword",
"supersecret=passw0rd"
],
"certificates": [
"${ceptor.home}/config/extra.cer",
"${ceptor.home}/config/other.cer",
"-----BEGIN CERTIFICATE----\nxxxxxxxxxyyyyyyyyxxxxx\n-----END CERTIFICATE----"
],
"entries": [
{
"name": "Name used as alias",
"privatekey": "PEM encoded RSA private key - possibly encrypted/obfusciated using password encryption - used to specify keys/certs only via configuration instead of requiring them to be loaded from external files",
"certificates": [
"PEM encoded certificate, or filename to load certificate from",
"additional PEM encoded certificate or filename",
".... all certificates are combined into a single entry within the keystore - so one certificate chain"
]
"certificate": "Ignored if 'certificates' is present - can otherwise contain a certificate if present, can either be PEM encoded, or filename (or semicolon separated filenames) of files to load certificates from",
"publickey": "Can contain a public key if present, can either be PEM encoded, or filename (or semicolon separated filenames) of files to load certificates from"
}
]
}
User interface configuration
Here is examples of the user interface for prompting for keystore information - note that depending on individual screens, not all might contain all the fields that the JSON has -e.g. if a screen is prompting for certificates only needed for validation, the fields with private keys are not shown.
Also note, that for Identity Providers, often you do not need to define they keys at all - instead you simply configure the URL to where to find the Federation Metadata, and the required certificates will be read periodically from the metadata URL.
If online access to the URL is not possible, e.g. due to firewall restrictions, you can also paste the federation metadata in to the configuration manually.
The keystore is configured in a JSON object called keystore within the service provider's JSON object.
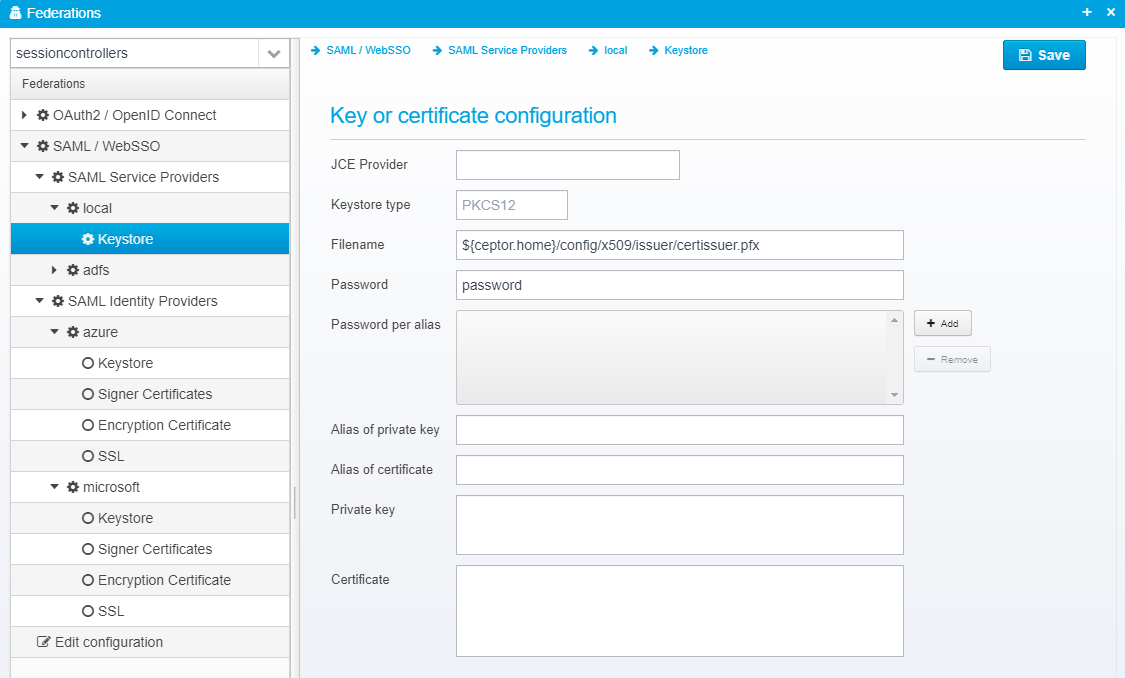
Key or certificate configuration
JCE Provider
Name of JCE provider - if left blank, platform default is used. Can be set to e.g. Luna to support hardware crypto providers assuming Luna JCE provider is installed.
Default: None
JSON key is provider
Keystore type
Keystore type, usually PKCS12 or JKS
Default: PKCS12
JSON key is type
Filename
Name of file to load keystore from - note that some keystores, e.g. Luna does not have a file
Default: None
JSON key is file
Password
Password for the keystore - can be encrypted, see Encrypting or Obfuscating Passwords
Default: None
JSON key is password
Password per alias
This is only needed if you have specific aliases in your keystore which have passwords that differ from the main keystore password - it allows you to specify a password for each alias specifically.
Default: None
JSON key is password.per.alias - this is a JSON Array with the format alias=password
Alias of private key
If provided, only the private key with the specified alias will be loaded.
Default: None
JSON key is alias.privkey
Alias of certificate
If provided, only the certificate with the specified alias will be loaded
Default: None
JSON key is alias.cert
Private key
Allows you to provide the private key as an RSA key in PKCS#8 format by pasting it directly.
Default: None
JSON key is privatekey
Certificate
Allows you to provide the certificate as Base64 encoded DER by pasting it directly instead of loading it from a keystore.
Default: None
JSON key is certificate
Public key
Allows you to provide the public key directly - this is only available for keystores used within OpenID Connect / JWT token configurations.
Note: Requires Ceptor v6.5.11+
Default: None
JSON key is publickey
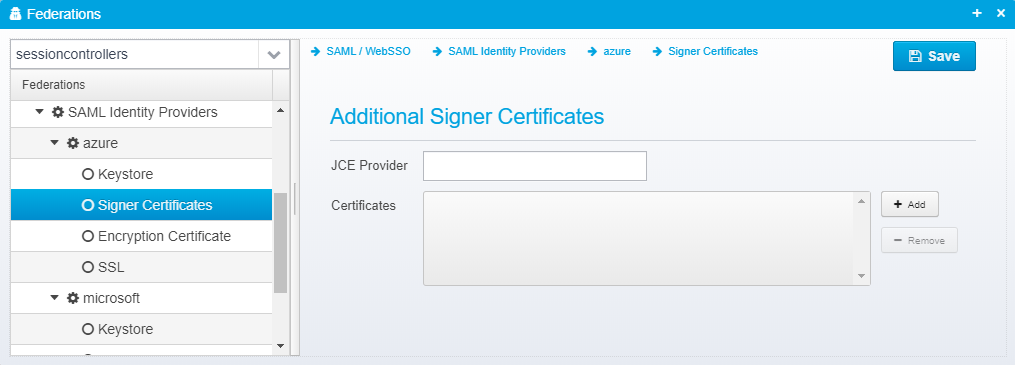
Certificates
Provide a list of filenames or certificates directly within the configuration.
Default: None
JSON key is certificates - which is a JSON Array of strings, each containing a filename of a certificate in .cer (binary or base64 encoded), .der or .p7b format or the certificate itself, if starting with -----BEGIN CERTIFICATE-----
© Ceptor ApS. All Rights Reserved.