...
WebLogic's security can be extended by creating WebLogic Security Plugins, which uses Oracle's Security Services Provider Interface (SSPI). Ceptor provides plugins that integrates with these plugins.
Oracle provides documentation on their plugins in their WebLogic documentation – there you can find additional detail about the possibilities with them.
Ceptor implements several types of plugins, including Authentication, Authorization, RoleMapper and Adjudicator. Not all plugins need to be used, typically only the Authentication plugin is required.
Authentication Provider (All versions)
The Authentication provider provides authentication only – it is meant to be used in connection with the Ceptor Gateway. The gateway then inserts the session ID in an authorization http header, and WebLogic will then provide the Ceptors session ID to the plugin as userid, and the plugin will then use it for authenticating the user.
Identity Provider (All versions)
The Identity provider works together with the Authentication Provider, and picks up Ceptor's session ID from the request attributes.
Authorization
...
Provider (WebLogic 8, 10, 11)
Ceptor's Authorization provider can make authorization decisions if the default J2EE way of authorizing based on deployment descriptors and roles is not sufficient. Any ACL defined in Ceptor will be checked against the corresponding WebLogic resource, which includes JNDI, EJB, JDBC and portlets. Please consult Oracle's documentation for details about the format of the WebLogic resources.
...
RoleMapper (WebLogic 8, 10, 11)
The RoleMapper is able to provide mapping between users and roles – this information is then used in e.g. HttpServletRequest.isUserInRole() calls by WebLogic. Ceptor will map group names directly to role names, if this plugin is installed.
Adjudicator (WebLogic 8, 10, 11)
The Adjudicator plugin is only required if multiple authorization plugins are installed, and decisions made by Ceptor's authorization plugin should be favoured above decisions made by other authorization plugins.
Installation of Security Providers
WebLogic 10/11
Installation is relatively straightforward, just copy the file wlPPSecurityProviders.jar to the directory /bea/weblogic81/server/lib/mbeantypes (or equivalent for your version) directory – there WebLogic will be able to see the new security providers.
Then, add the file wlPPprincipal.jar to the system classpath of this and all other weblogic instances that this weblogic server shares trust with. It contains a principal class that weblogic will serialize and send to other weblogic servers that it shares trust with.
Make sure that you also have CeptorAgent.jar, and log4j.jar in your classpath, or you will get a ClassNotFoundException when attempting to add the authenticator.
Note for WebLogic 10 and newer: Oracle WebLogic 10 is not compatible with earlier versions, so you need to use wl10PPSecurityProviders.jar instead of wlPPSecurityProviders.jar it has the same functionality for WebLogic 10.
For WebLogic 11, 12, 14 and newer, use wl11PPSecurityProviders.jar
...
| Code Block |
|---|
CeptorAgent.jar
reload4j-1.2.20.jar
wlPPprincipal.jar
logback-core-1.2.10.jar
logback-classic-1.2.10.jar
slf4j-api-1.7.36.jar |
WebLogic 12/14
The major difference between 12/14 and the earlier versions is that logging no longer requires log4j, but it uses SLF4j - same as the Ceptor Agent - and in addition a newer version of the SSPI interface is supported.
The authorization, rolemapper and adjudicator plugins are no longer present - instead, authorization relies solely on user/group membership supplied by Ceptor and is used with standard authorization plugins.
Copy the file wlPPSecurityProviders12.jar or wlPPSecurityProviders14.jar to the directory server/lib/mbeantypes directory – there WebLogic will be able to see the new security providers.
Then, add the file wlPPprincipal.jar to the system classpath of this and all other weblogic instances that this weblogic server shares trust with. It contains a principal class that weblogic will serialize and send to other weblogic servers that it shares trust with.
In addition, you need to install the Ceptor Agent and its dependencies - an easy way is to copy these files into the domain lib directory (be sure to use the appropriate version that might be different in your Ceptor release):
| Code Block |
|---|
CeptorAgent.jar wlPPprincipal.jar logback-core-1.2.10.jar logback-classic-1.2.10.jar slf4j-api-1.7.36.jar |
After installation of files is complete
Be sure to also supply the Ceptor Agent configuration - either in system properties or ptserver.properties file available in the classpath.
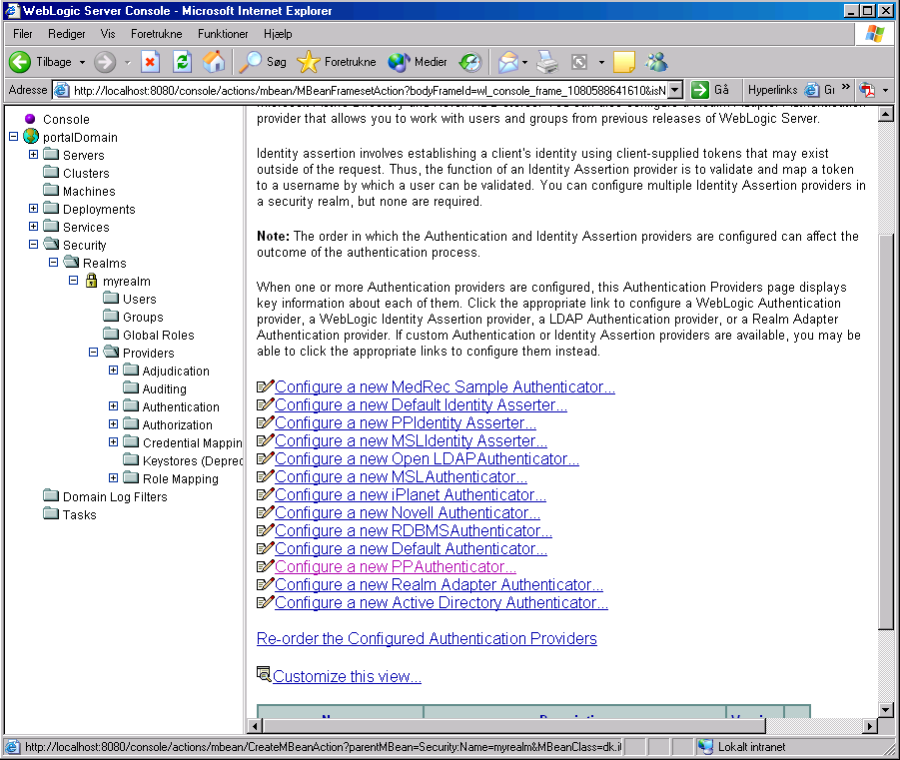
After restarting WebLogic, go to the administration console and add the authentication provider "PPAuthenticator" – first go to
_Security->Realms->myrealm->Providers->Authentication_
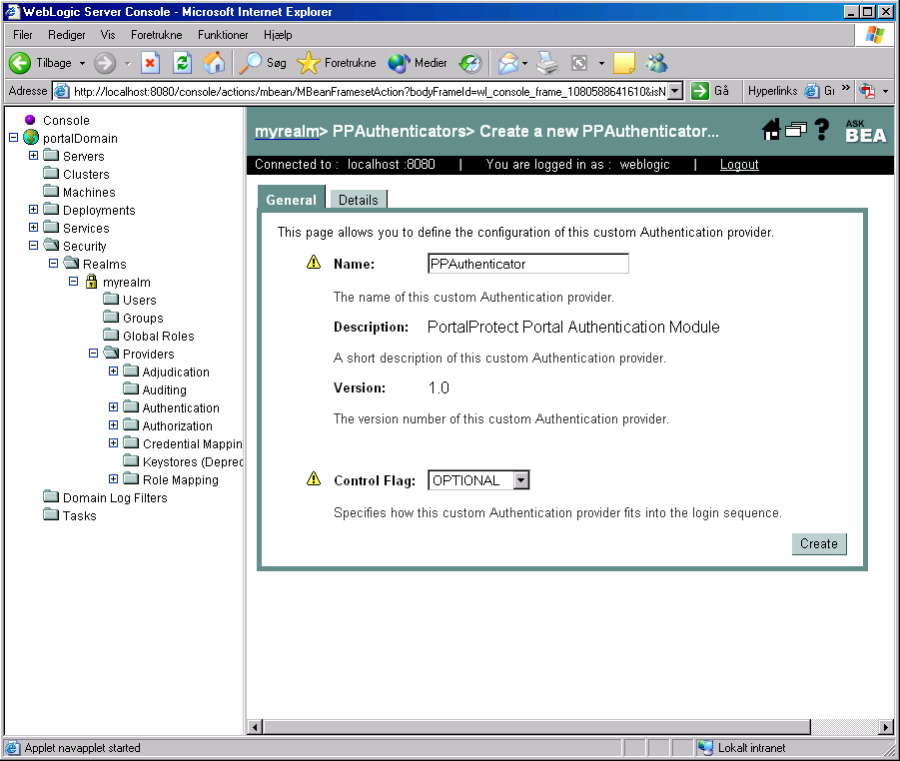
and then click on "Configure a new PPAuthenticator"
After clicking on "Configure a new PPAuthenticator" the following screen comes up, simple click on "Create" and that's it, the new Ceptor authenticator is now installed.
Now, make sure to change the "Control Flag" to "OPTIONAL" on the "DefaultAuthenticator" – otherwise WebLogic won't accept the PP Authenticators login.
In order to use the plugin, you need to configure the Ceptor gateway to add the Authorization header to the HTTP request before sending it to the WebLogic server – this will enable WebLogic to call the PP Authentication provider with the session ID as userid.
The PP Authentication provider will then look at the session, and if the user is authenticated, it will log him into WebLogic as well. Note that WebLogic will only see the user as authenticated, once his PP session is authenticated, so role-checking functions such as isUserInRole() will only work on authenticated users.
...