...
| Code Block | ||||
|---|---|---|---|---|
| ||||
{
"listen": [
{
"address": "0.0.0.0",
"scheme": "http",
"port": 8000,
"useproxyprotocol": true,
"useforwardedheader": false
},
{
"address": "0.0.0.0",
"scheme": "ajp",
"port": 8001
},
{
"scheme": "https",
"address": "0.0.0.0",
"port": 8443,
"sslcontext": {
"ssl.provider": "SunJSSE",
"ssl.protocol": "TLS",
"wantclientauth": true,
"needclientauth": false,
"allowrenegotiate": false,
"sni.requirematch": false,
"excludeprotocols": "SSL,SSLv2,SSLv2Hello,SSLv3",
"includeprotocols": "TLSv1.2,TLSv1.1",
"excludeciphersuites": ".*NULL.*,.*RC4.*,.*MD5.*,.*DSS.*",
"includeciphersuites": "TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_,SSL_RSA_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA",
"keystore.type": "JKS",
"keystore.provider": "SUN",
"keystore.file": "${portalprotect.home}/dispatcher/portalprotect.key",
"keystore.password": "changeit",
"useciphersuites.order": true,
"truststore.type": "PKCS12",
"truststore.provider": "BC",
"truststore.file": "${portalprotect.home}/config/x509/issuer/certissuer.pfx",
"truststore.password": "password",
"keystores": [{
"name": "second",
"password.per.alias": [],
"certificates": [],
"entries": [
{
"name": "ca",
"privatekey": "-----BEGIN PRIVATE KEY-----\nMIIEvQIBADA...removed...peGYffSn9E8=\n-----END PRIVATE KEY-----\n",
"certificates": ["-----BEGIN CERTIFICATE-----\nMIIESTCC... removed...\n-----END CERTIFICATE-----\n"]
},
{
"name": "root",
"privatekey": "-----BEGIN PRIVATE KEY-----\n...removed...DlqjF8s=\n-----END PRIVATE KEY-----\n",
"certificates": ["-----BEGIN CERTIFICATE-----\nMIIFUDCCAz...removed...HGSDk=\n-----END CERTIFICATE-----\n"]
}
]
}],
"truststores": [{
"name": "secondtrust",
"password.per.alias": [],
"certificate": "-----BEGIN CERTIFICATE-----\nMIIDrzCCApegAwIBA...removed...40KPMbp1ZWVbd4=\n-----END CERTIFICATE-----"
}]
}
}
]
}
|
Configuration via Ceptor Console
...
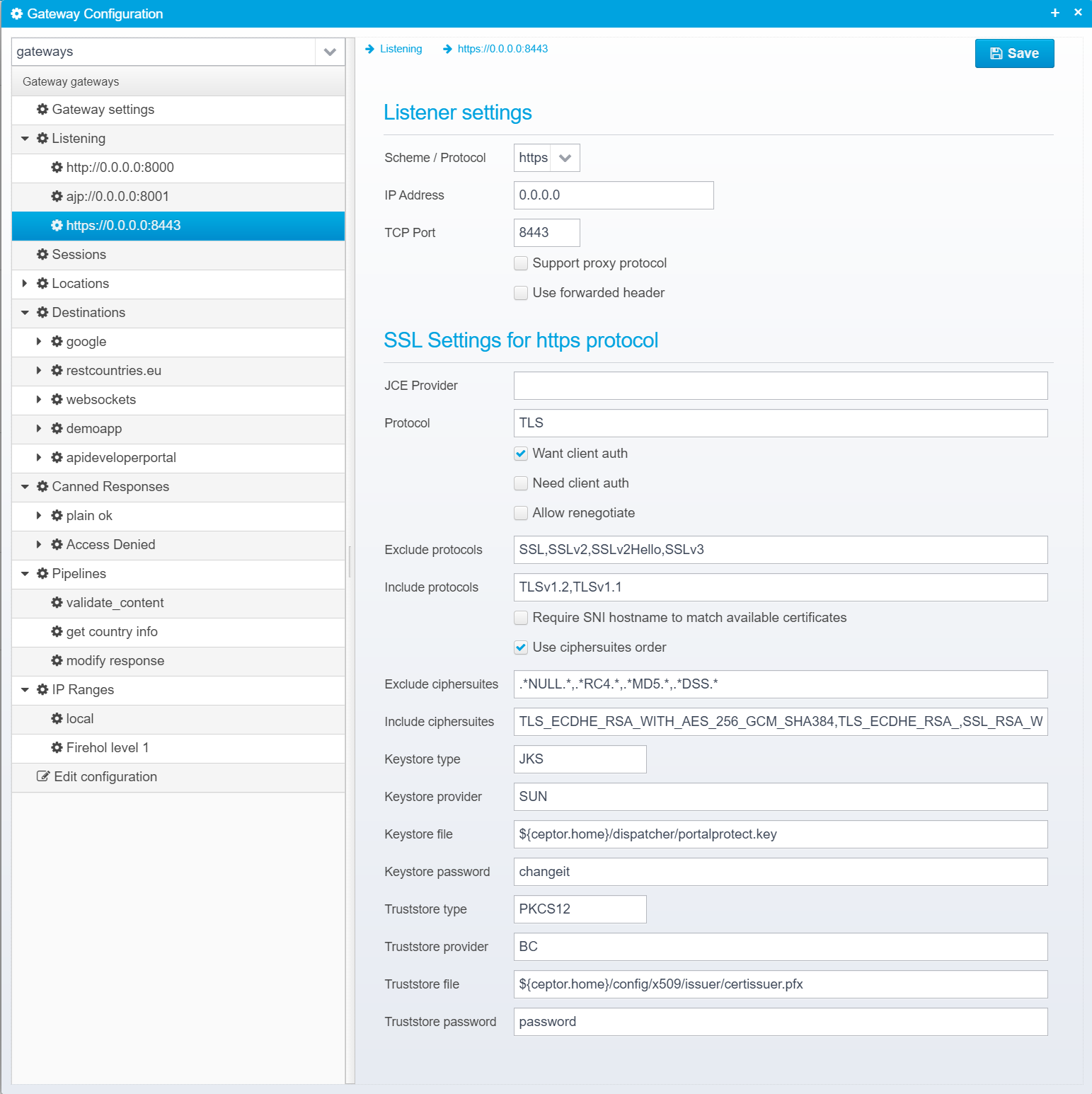
Once created, each listener has these properties which you can edit - note that the SSL options are only used if the protocol is set to https.
Listener settings
...
- https
HTTP over SSL. - http
Unencrypted HTTP. - ajp
Apache JServ Protocol - a binary unencrypted protocol used by some proxy servers, such as Apache or nginx.
Use of ajp is to be considered experimental and not generally recommended by Asseco.
Note that for HTTP, all current versions of the HTTP protocol are supported by the gateway, meaning 0.9/1.0/1.1 and HTTP/2.
...
Default: none
JSON key: keystore.password
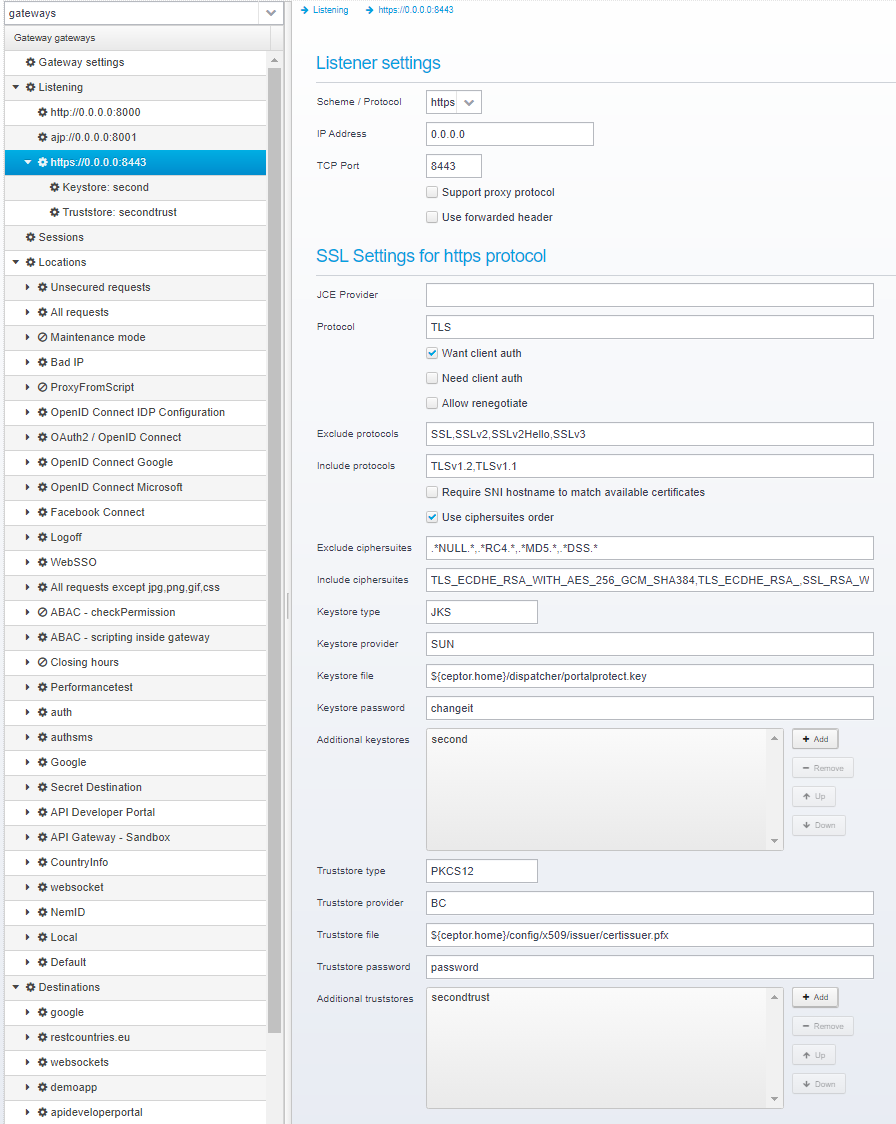
Additional keystores
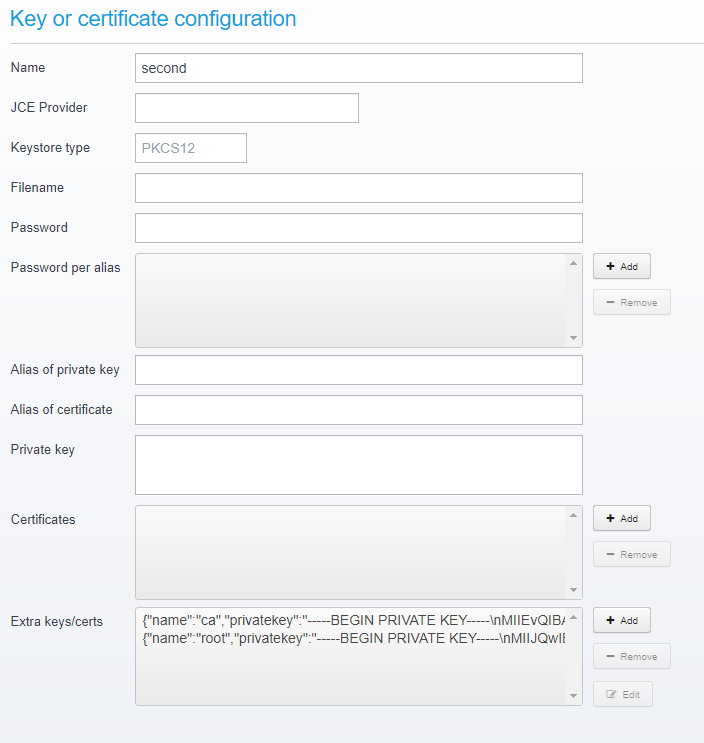
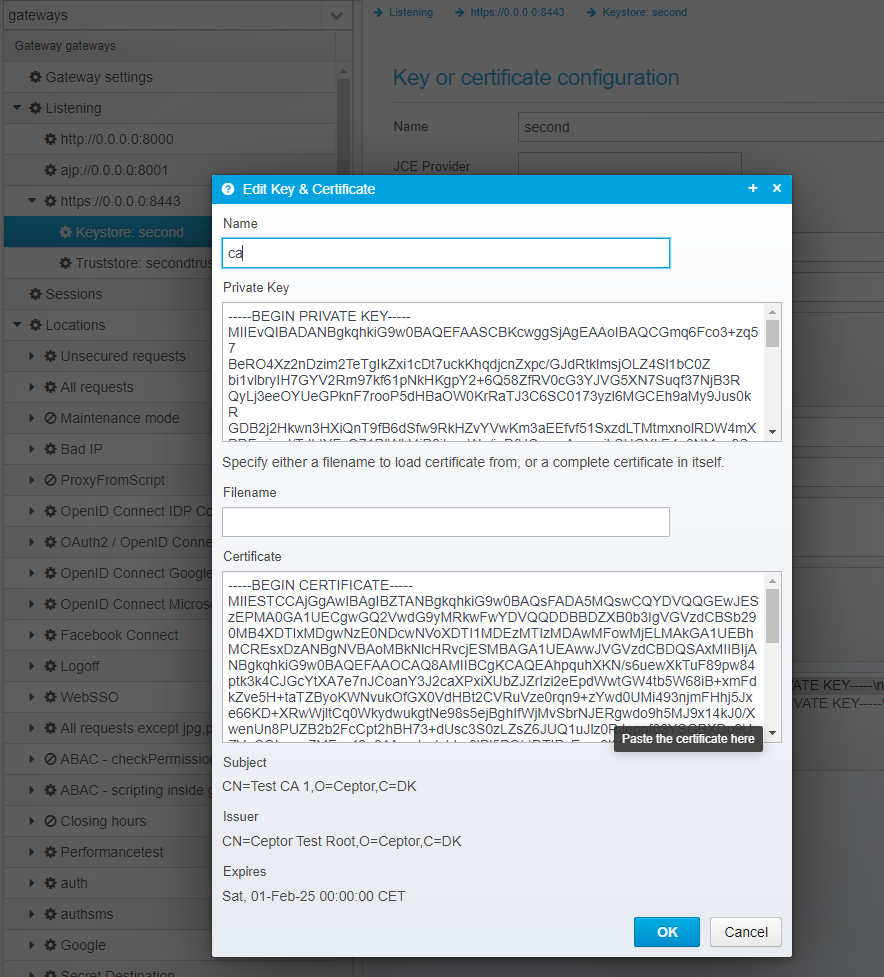
This allows you to define additional keystores to load certificates from, or you can add the certificates and private keys directly to the configuration without needing to load them from external files. (Requires minimum version 6.5.0)
| Tip |
|---|
Ceptor Gateway combines multiple keystores into one logical keystore - so if you load keys and certificates from multiple places using multiple providers, e.g. from both files and from hardware HSMs, then both types can be used simultaneously. |
In this example above, you can define a new keystore of a different type and provider, and you can define extra keys and certificates directly without loading them from external sources.
For more specific information about the JSON layout, refer to: Keystore configuration
Default: none
JSON key: keystores
Truststore type
Type of truststore, e.g. PKCS12, or JKS (default PKCS12)
All certificates found in this keystore will be loaded and used as accepted CA certificates when prompting for SSL client certificates.
Note that authentication is not done solely on these certificates - authentication of SSL client certificates is done by authentication plugins in the Ceptor Session Controller which have their own set of allowed and configured root CAs.
...
Default: none
JSON key: truststore.password
Additional truststores
This allows you to define additional keystores to load trusted certificates from, or you can add the certificates directly to the configuration without needing to load them from external files. (Requires minimum version 6.5.0)
Default: none
JSON key: keystores