...
Default: None
JSON key is attributes - as a JSON Array containing string values
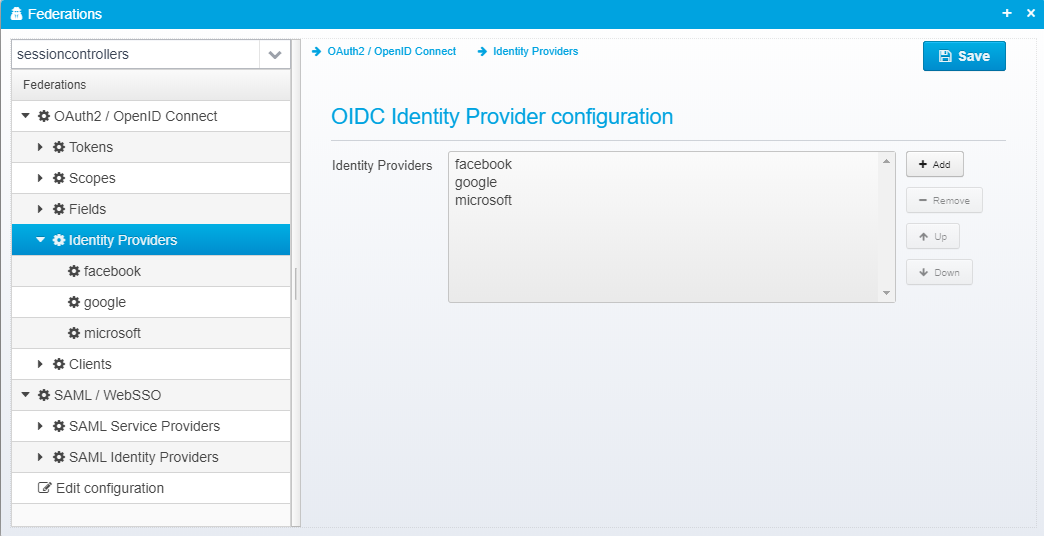
Identity Providers
When Ceptor authenticates users using foreign OpenID Connect Providers, you can define the authentication providers here.
These Identity Providers are then used within the Ceptor Gateway - see Location - Authentication for information about how to configure the gateway to use these identity providers under specific conditions.
Ceptor has custom support for some identity providers which almost are following the OpenID Connect standard, such as LinkedIn and Facebook.
Configuration for identity providers are stored in a JSON Array called openid.identityproviders - each identity provider is a separate JSON Object.
| Code Block | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
"openid.identityproviders": [
{
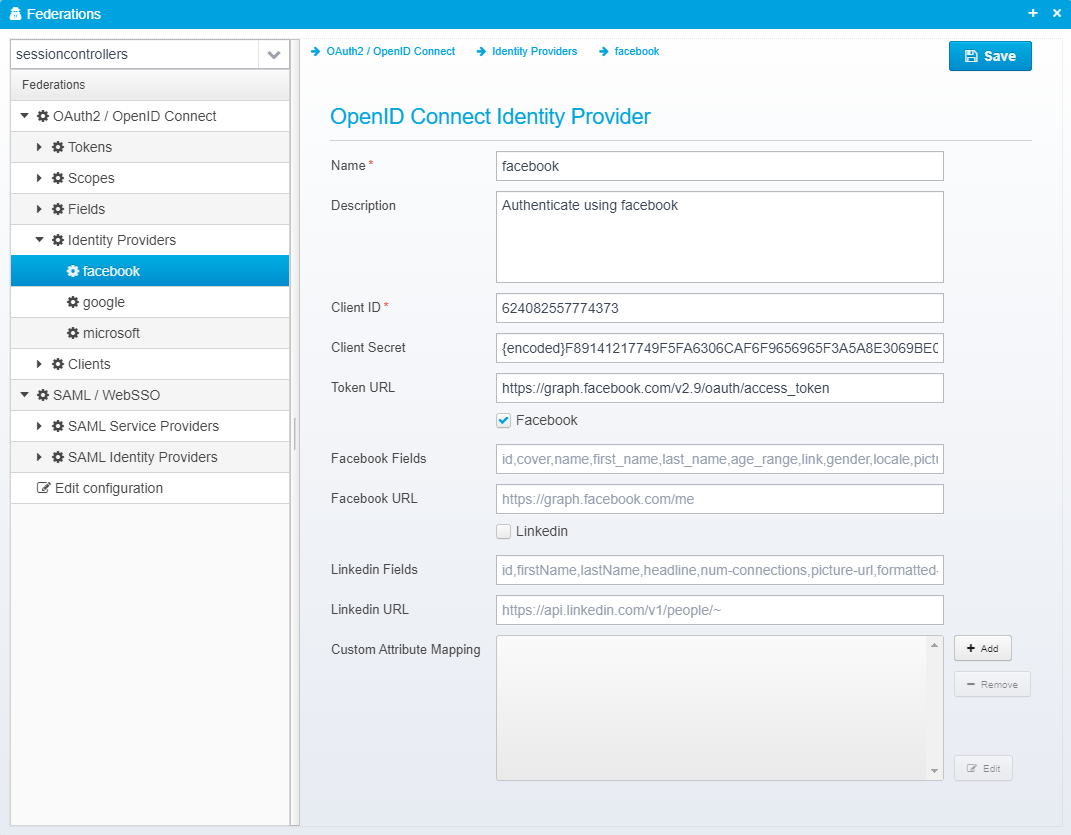
"name": "facebook",
"description": "Authenticate using facebook",
"clientid": "624082557774373",
"secret": "{encoded}F89141217749F5FA6306CAF6F9656965F3A5A8E3069BE032136125F3A4B27183",
"tokenurl": "https://graph.facebook.com/v2.9/oauth/access_token",
"facebook": true,
"linkedin": false,
"fieldmappers": []
},
{
"name": "google",
"description": "Google as an identity provider",
"clientid": "371213948273-79eceu24cm64ft69pln0hk2lfapok1bq.apps.googleusercontent.com",
"secret": "{encoded}806F9FE0C7CBC28D5777D6DE91772DA4961482568956695A",
"tokenurl": "https://accounts.google.com/o/oauth2/token",
"facebook": false,
"linkedin": false,
"fieldmappers": []
},
{
"name": "microsoft",
"description": "Authenticate using microsoft as identity provider",
"clientid": "317190f9-efec-4307-beb9-7f8380a8ae16",
"secret": "{encoded}9EED6C32369008FE6F3DC027CC0C2195137300594A2620",
"tokenurl": "https://login.microsoftonline.com/common/oauth2/v2.0/token",
"facebook": false,
"linkedin": false,
"fieldmappers": []
}
]
|
OpenID Connect Identity Provider
Name
Identity provider name
...
| Code Block | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
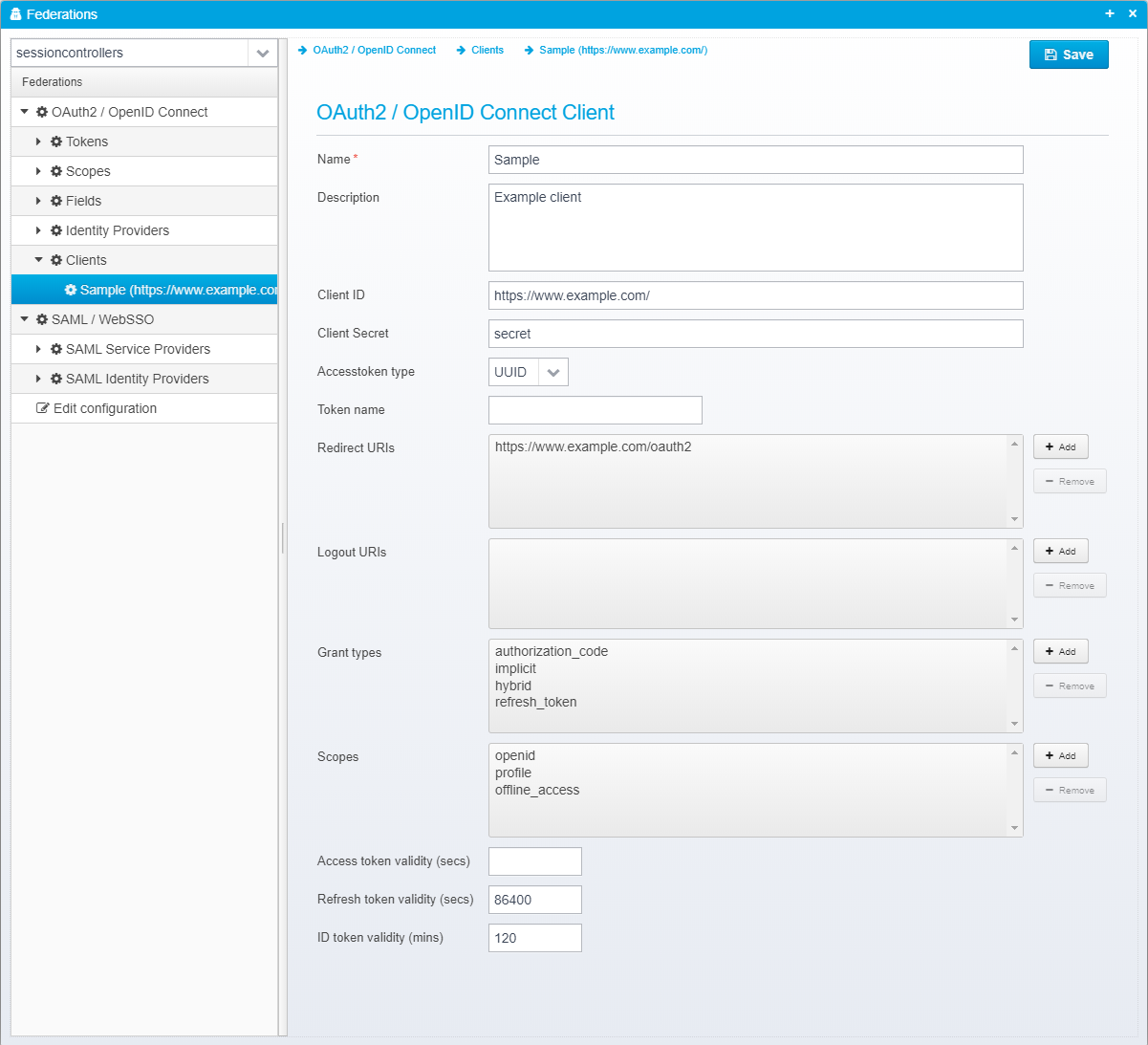
"oauth2.clients": [{
"name": "Sample",
"client_id": "https://www.example.com/",
"description": "Example client",
"client_secret": "secret",
"accesstoken_type": "UUID",
"allowed_uris": ["https://www.example.com/oauth2"],
"allowed_logout_uris": [],
"valid_grant_types": [
"authorization_code",
"implicit",
"hybrid",
"refresh_token"
],
"allowed_scopes": [
"openid",
"profile",
"offline_access"
],
"refreshtoken_validity_seconds": 86400,
"maximum_idtoken_expiration_minutes": 120
}]
|
OAuth2 / OpenID Connect Client
Name
Name of OAuth 2 / OpenID Connect client or partner.
Default: None
JSON key is name
Description
Optional description
Default: None
JSON key is description
Client ID
Client ID - must be unique across all configured clients.
Default: None
JSON key is client_id
Client Secret
Client secret - may be encrypted/obfuscated.
Default: None
JSON key is client_secret
Accesstoken type
Type of access token to issuer - either UUID or JWT - if UUID, the token itself does not contain any attributes, and the OAuth2 introspection (or userinfo) URL must be called using the access token to get any of the attributes related to it. If the type is JWT, the access token is similar to the ID token a signed JWT token containing the attributes itself.
Default: None
JSON key is accesstoken_type
Token name
Name of token to use if not the default -allows you to select specific tokens (and thus specific keys, content etc.) for specific clients.
Default: None
JSON key is tokenname
Redirect URIs
List of valid redirect URIs for this client/partner
Default: None
JSON key is allowed_uris as a JSON array of strings
Logout URIs
List of valid logout URIs for this client/partner
Default: None
JSON key is allowed_logout_uris as a JSON array of strings
Grant types
List of valid grant types to allow for this client. If this list is empty, all types are allowed, otherwise only the specified ones are allowed for this client to use.
Default: None
JSON key is valid_grant_types
Scopes
If not empty, this list restricts which scope names the client is allowed to use.
Default: None
JSON key is allowed_scopes as a JSON array of strings
Access token validity (secs)
If specified, can override the default validity period of issued access tokens.
Default: None
JSON key is accesstoken_valid_seconds
Refresh token validity (secs)
If specified, can override the default validity period of issued refresh tokens.
Default: None
JSON key is refreshtoken_validity_seconds
ID token validity (mins)
If specified, can override the default validity period of issued ID tokens.
Default: None
JSON key is maximum_idtoken_expiration_minutes