...
Attributes to send as claims to Service Provider.
See SAML / JWT Attributes / Claims for information of content.
...
Default: None
JSON key is samlrequest
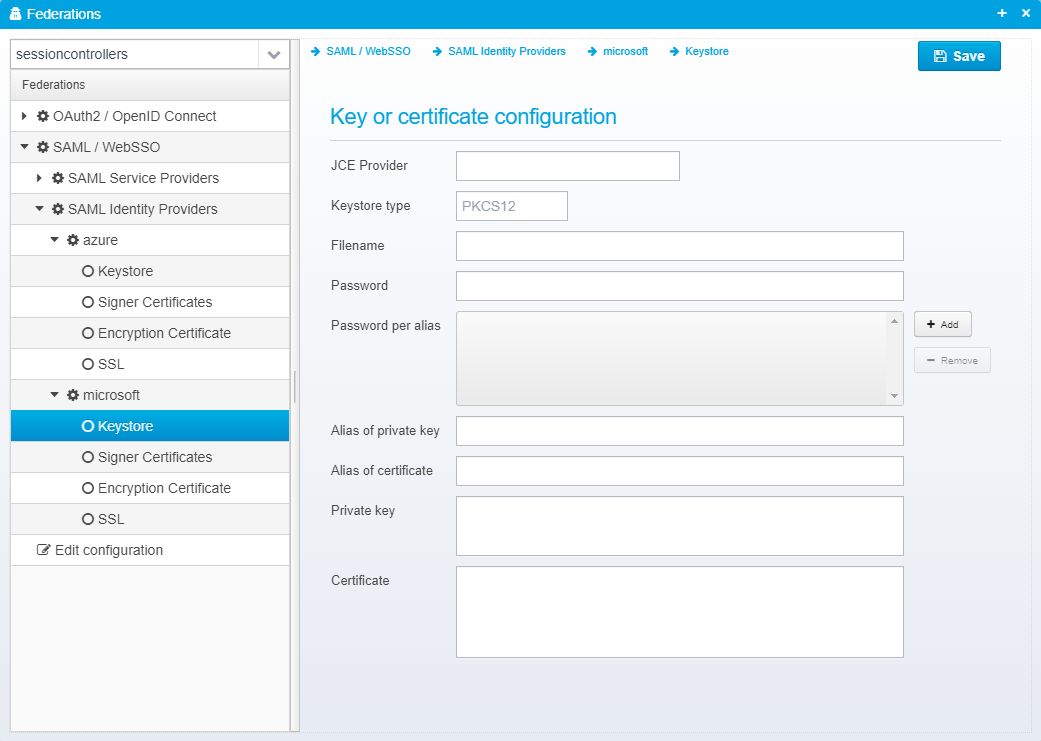
Keystore
The keystore is configured in a JSON object called keystore within the identity provider's JSON object.
Key or certificate configuration
JCE Provider
Name of JCE provider - if left blank, platform default is used. Can be set to e.g. Luna to support hardware crypto providers assuming Luna JCE provider is installed.
Default: None
JSON key is provider
Keystore type
Keystore type, usually PKCS12 or JKS
Default: PKCS12
JSON key is type
Filename
Name of file to load keystore from - note that some keystores, e.g. Luna does not have a file
Default: None
JSON key is file
Password
Password for the keystore - can be encrypted, see Encrypting or Obfuscating Passwords
Default: None
JSON key is password
Password per alias
This is only needed if you have specific aliases in your keystore which have passwords that differ from the main keystore password - it allows you to specify a password for each alias specifically.
Default: None
JSON key is password.per.alias - this is a JSON Array with the format alias=password
Alias of private key
If provided, only the private key with the specified alias will be loaded.
Default: None
JSON key is alias.privkey
Alias of certificate
If provided, only the certificate with the specified alias will be loaded
Default: None
JSON key is alias.cert
Private key
Allows you to provide the private key as an RSA key in PKCS#8 format by pasting it directly.
Default: None
JSON key is privatekey
Certificate
Allows you to provide the certificate as Base64 encoded DER by pasting it directly instead of loading it from a keystore.
Default: None
JSON key is certificate
| Info |
|---|
See also Keystore configuration for additional details of configuring keystores when using federation. |
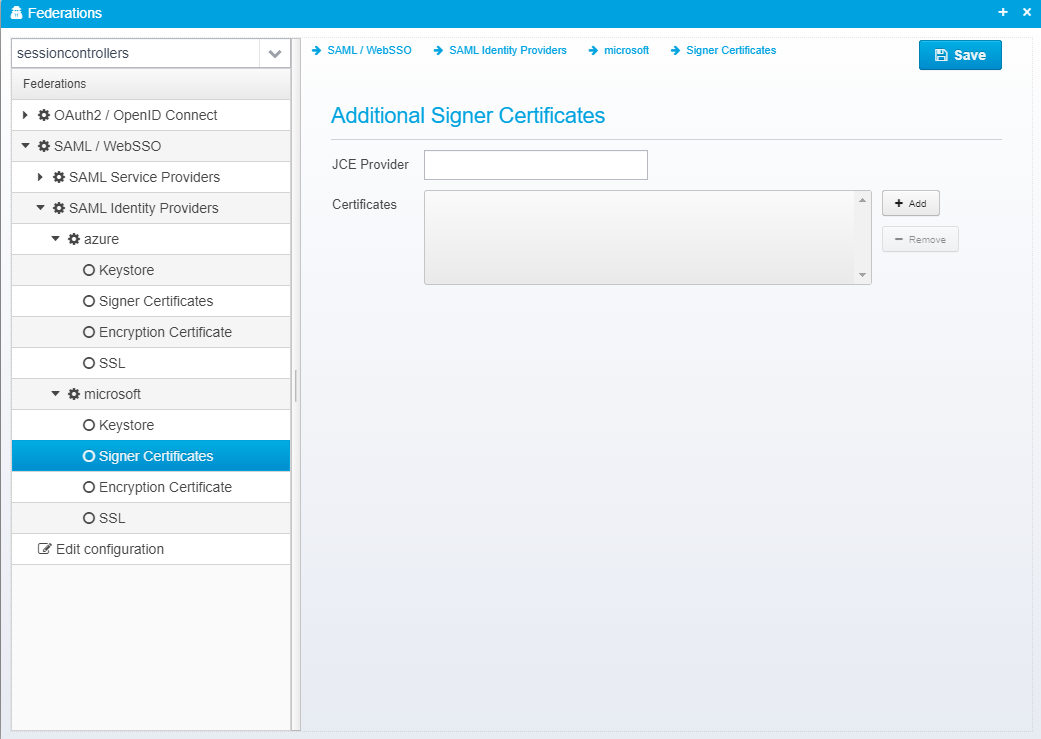
Signer Certificates
This configuration is stored in the JSON Object signer.certificates inside the identity provider JSON.
Additional Signer Certificates
JCE Provider
Name of JCE provider - if left blank, platform default is used. Can be set to e.g. Luna to support hardware crypto providers assuming Luna JCE provider is installed.
Default: None
JSON key is provider
Certificates
Provide a list of filenames or certificates directly within the configuration.
This allows you to specify additional trusted signer certificates for use when validating signed SAML Response - note that if you already are loading federation metadata from online, or have it pasted, these certificates configured here are in addition to the ones from the metadata.
Default: None
JSON key is certificates - which is a JSON Array of strings, each containing a filename of a certificate in .cer (binary or base64 encoded), .der or .p7b format or the certificate itself, if starting with -----BEGIN CERTIFICATE-----
| Info |
|---|
See also Keystore configuration for additional details of configuring keystores when using federation. |
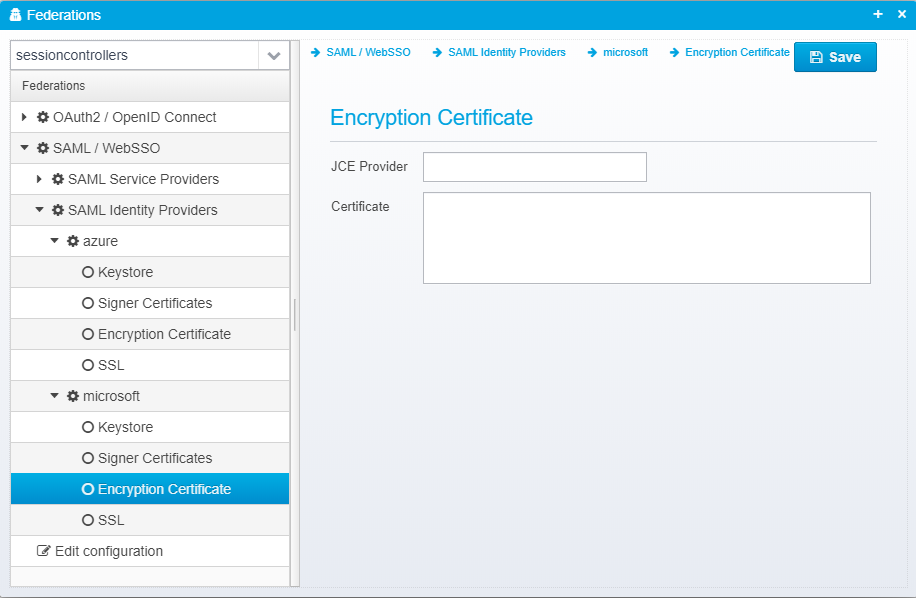
Encryption Certificate
This configuration is stored in the JSON Object encryption.certificates inside the identity provider JSON.
Encryption Certificate
JCE Provider
Name of JCE provider - if left blank, platform default is used. Can be set to e.g. Luna to support hardware crypto providers assuming Luna JCE provider is installed.
Default: None
JSON key is provider
Certificates
If you wish to specify an encryption certificate for use when encrypting a SAML request, you can do so here - normally you would use federation metadata for this, but it can be specified manually.
Default: None
JSON key is certificate
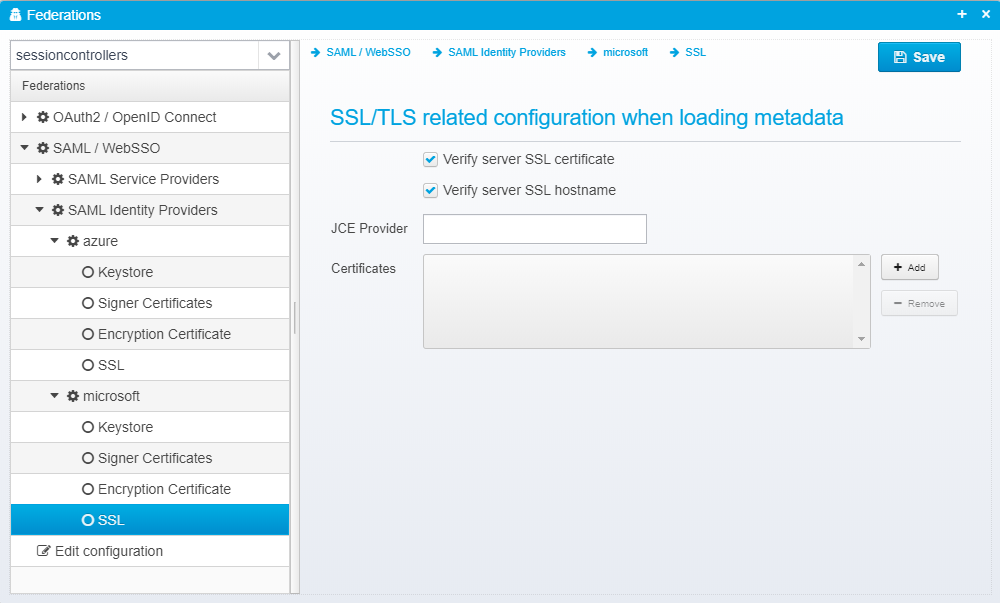
SSL
This configuration is stored in the JSON Object ssl inside the identity provider JSON.
SSL/TLS related configuration when loading metadata
Verify server SSL certificate
Uncheck to disable SSL server certificate validation - if checked, SSL server certificates must either match installed root certificates in the JVM, or one of the additionally specified certificates.
Default: true
JSON key is verify.server.cert
Verify server SSL hostname
Uncheck to disable SSL hostname verification - if checked, the SSL hostname is matched up against the SSL server certificate.
Default: true
JSON key is verify.hostname
JCE Provider
Name of JCE provider - if left blank, platform default is used. Can be set to e.g. Luna to support hardware crypto providers assuming Luna JCE provider is installed.
Default: None
JSON key is provider - inside accepted.certificates JSON object within the ssl object.
Certificates
Provide a list of filenames or certificates directly within the configuration.
This allows you to specify additional SSL server issuer trust certificates certificates for use when validating signed SSL server certificate when retrieving metadata from remote
Default: None
JSON key is certificates- inside accepted.certificates JSON object within the ssl object.